Real Time Monitoring System
The Swiss army-knife to have a view on your infrastructure.
What every organization should monitor ?
Overview
The 3TS RTMS is a lightweight, containerized security probe designed for modern, distributed IT infrastructures. Unlike traditional scanners that require complex VPNs, heavy firewall configurations, or manual updates, 3TS RTMS operates on a “Pull” architecture.
It sits quietly inside your network, autonomously mapping assets and detecting vulnerabilities, while you manage everything from a centralized Cloud Dashboard. Whether you manage one office or a hundred remote sites, 3TS RTMS gives you a unified view of your security posture without the operational headache.
Architecture
The 3TS RTMS is a lightweight, containerized security probe designed for modern, distributed IT infrastructures. Unlike traditional scanners that require complex VPNs, heavy firewall configurations, or manual updates, 3TS RTMS operates on a “Pull” architecture.
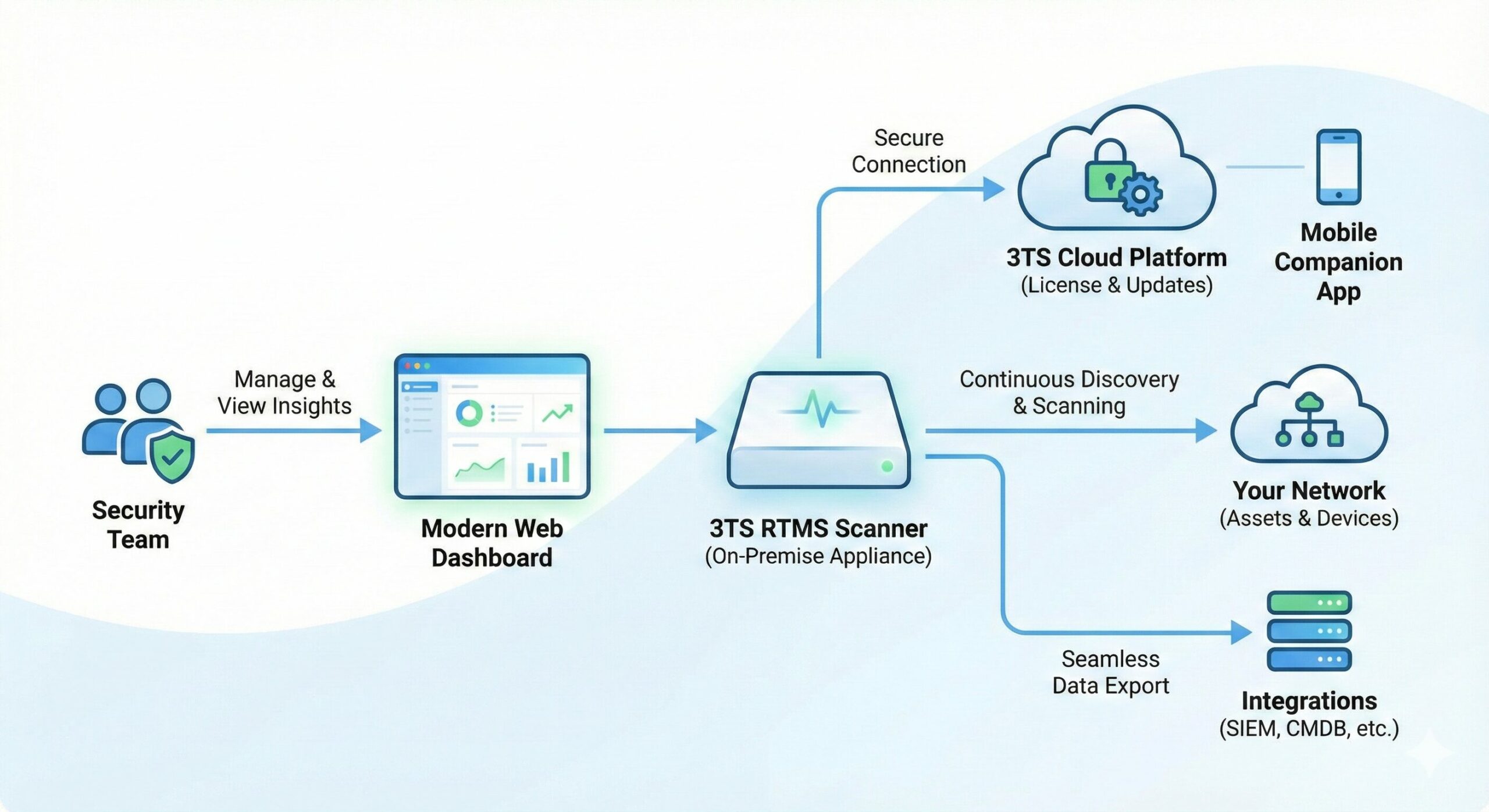
Key Features
1. Asset Discovery & Mapping
Stop guessing what’s on your network. The scanner utilizes an advanced Nmap-based engine to perform rapid port scanning and OS fingerprinting.
-
Real-time Inventory: Automatically populate your CMDB (compatible with iTop).
-
Rogue Device Detection: Get alerted immediately when an unknown device connects to your Wi-Fi or LAN.
2. Proactive Vulnerability Scanning (CVE)
Don’t wait for a breach to patch your systems.
-
CVE Detection: Identifies outdated services and potential security holes against the latest NIST databases.
-
Risk Scoring: Prioritize fixes based on severity.
-
Note: Advanced CVE scanning is available in the Enterprise Edition.
3. “Zero-Touch” Remote Configuration
Deploy once, manage forever. You never need to SSH into the scanner or visit the client site.
-
Heartbeat Architecture: The scanner periodically polls the 3TS Cloud for new instructions.
-
Dynamic Targeting: Change scan targets (IP ranges, subnets) remotely via your web dashboard.
-
Firewall Friendly: Works entirely via outbound HTTPS (Port 443). No inbound firewall ports required.
4. Enterprise Integrations
Your data belongs in your tools, not in a silo.
-
SIEM Ready: Native forwarding to Splunk (via HEC) for log aggregation and alerting.
-
CMDB Sync: Keep your asset management database up to date automatically.
-
Automated Reporting: Generate professional PDF security reports for auditors or management.
How it Works
The 3TS RTMS is built on a “Download & Forget” philosophy:
-
Deploy: Pull our secure Docker Image and launch it with your unique License Key.
-
Connect: The scanner authenticates with the 3TS Cloud using a cryptographic Hardware ID.
-
Scan: It downloads its configuration profile and begins mapping your local network.
-
Report: Results are encrypted and pushed to your Dashboard, SIEM, or CMDB.
Security First: The application logic is compiled and tamper-proof. Local configuration caches are protected by HMAC signatures to prevent unauthorized modification.
Editions
We offer a flexible model that grows with your needs. The software is the same; your license key unlocks the power.
| Feature | Demo / Community | Enterprise Edition |
| Deployment | Docker Container | Docker Container |
| Network Discovery | Basic (Ping/ARP) | Deep (Service Versioning) |
| Max Targets | Up to 10 IPs | Unlimited |
| Vulnerability Scan | ❌ Locked | ✅ Full CVE Analysis |
| Reporting | On-Screen Only | ✅ PDF Export & API |
| Remote Config | ❌ Manual | ✅ Cloud Managed |
| Support | Community | 24/7 Priority |
System Requirements
-
OS: Linux (Ubuntu, Debian, CentOS), macOS, or Windows (via WSL2).
-
Runtime: Docker Engine & Docker Compose.
-
Hardware: Minimal resource footprint. Runs smoothly on 1 vCPU / 512MB RAM.
-
Network: Outbound Internet access (HTTPS) to 3TS Cloud.

